How To Setup A Phishing Campaign Using GoPhish - Part 3
- Hellfire0x01

- Sep 19, 2022
- 6 min read
Updated: Dec 6, 2022
Hey. In my previous blog, I demonstrated how we send phishing mail using the Gophish tool to the Innocent Daddy user. In this blog, let's dive into the Blue World, the defensive side, where we will analyze these phishing emails.
Before starting off, I was thinking to give you the high level overview of what phishing is, why phishing happens, and why it is necessary for us to analyze them? Those questions must be addressed.
Beginning with phishing, emailing a victim with malicious intent to obtain sensitive information, downloading a malicious file, etc.
Second, phishing happens because the overall goal of a phishing attack is usually to gain sensitive data such as logins and passwords from their victims in order to access the targeted network or company.
Finally, wouldn't it be awesome if everyone was an email ninja? It is really necessary to analyze emails because each successful hack in any company begins with a phishing email!

Special thanks to my dear friend 0xAsif, I was able to create an undetectable malicious word document, and attach it into email! Now, let's dive in!!
Humans are only as Strongest as their Weakest link
In any organization, even if every system is patched, internal/external infrastructure is secured, firewalls/HIPS/HIDS/NIDS/NIPS/EDR/XDR/SIEM etcetera are implemented, that doesn't mean employees are trained enough to stop malicious emails to sneak into their network. With just one mistake, that one click, would bring the whole organization to its knees.
Therefore, it is extremely necessary to educate as much people, may it be a CEO, a Manager, a Team Lead, or a Junior employee, or any individual with zero knowledge in cybersecurity.
Now let's get to the important part. When analyzing emails, we need to gather different kinds of IOCs, Indicators of Compromise. IOCs are artifacts that have been observed in relation to malicious activity.
Here are the list of IOC's we have to gather,
1. Email Artifacts:
- Sending Email Address
- Subject Line
- Recipient Email Addresses
- Sending Server IP & Reverse DNS
- Reply-To Address
- Date & Time
2. Web Artifacts:
- Full URLs
- Domain Names
3. File Artifacts:
- Attachment Name
- MD5, SHA1, SHA256 Hash ValueScenario #1
All right, scenario one. I am a student at Doofenshmirtz Evil University, and I applied to be a penetration tester for Secure Technology Company. Following my candidacy, I received LinkedIn's email (legit) the same day. But the next morning, I got the same correspondence as yesterday. But, this time, it seems very odd that I should not get the same e-mail twice. It piqued my concern. SUS!!

I therefore decided to allow content remotely to be visible in the email,

It's time for the hunt. In the beginning, I thought it was a legitimate email because there is literally not a single error in spelling, content, visuals, etcetera.

I looked at the sender's address, which is downright bizarre because such emails should come from LinkedIn <jobs-listings@linkedin.com>, but they came from phishmepleaseeehellfire@outlook.com. That made my suspect confirmed, so I start messing around with it by hovering the mouse pointer over the name of the company listed in the email. It pointed out the real URL in the hyperlink, hxxps://phishmepleaseeehellfire[.]cf/?rid=hs4SqBi

Let's collect the IOCs from that email. I opened the .eml file into the sublime text editor, and there we can see the source code for the email. Here we should look for the mentioned IOC (see above) that are marked in yellow:

Date - Date and Time at which the mail was received.
Sender's Address - Address where the mail came from.
Recipient's Address - Address which received the mail.
Subject-Line - Email Subject (The Heading).
IP Address - IP address of the system from which the mail was sent.
As we also have the IP address, let's do a WHOIS Lookup on this IP address,

This search reveals the IP address resolution host, which is c180-2.smtp-out.ap-south-1.amazonses.com, which means it originates from the AWS Simple Mail Service,
Reverse DNS - Resolved host obtained from IP address.
Now we must get this sp00ky URL which has been hyperlinked under the name of the named company. Then let's look for Source Technology (the company I applied for), and there we can see the sp00ky URL that's there,

Full URL - The complete URL which is received.
Root Domain - Only the main (base) domain.
From there, we can use a couple of online tools to check if this URL is malicious. These tools are:
URL2PNG - This web-based service will take a screenshot of the pasted URL and allow you to see what the web page looks like.
URLhaus - This online service will look through its database to determine whether the specified URL is malicious or not.
Wannabrowser - This online service lets you check HTTP response codes.
VirusTotal - This online service can be used to scan suspicious files, URLs to detect malicious software types, and malicious content using antivirus engines.
TalosIntelligence - This web-based service is similar to VirusTotal.
URLScan - It is used to analyze suspicious and malicious URLs.
Now, let's see what that complete URL looks like when somebody visits it (it is not accessible because the EC2 instance I used to send this email is destroyed, otherwise it would have shown us the website!). Add the URL, hxxps://phishmepleaseeehellfire[.]cf?rid=hs4SqBI

Imagine if there was a different (hypothetical) Full URL like hxxps://outlook-mail.phishmepleaseeehellfire.cf?rid=AsdjASDA23, then we must search for "Full URL" as well as "Root Domain", which is hxxps://phishmepleaseeehellfire.cf. But in this case, we don't need to because we have enough evidence that this email is malicious.
Similarly, we can use other online services as well to verify whether the URL is suspect or not.
From this mail, we were able to gather these IOCs,
Sender's Address: phishmepleaseeehellfire@outlook.com
Recipient's Address: daddyphishedme@outlook.com
Date: Thu, 8 Sep 2022 14:14:24 +0000
Subject-Line: You applied for Penetration Tester at Source Technology
IP Address: 76.223.180.2
Reverse DNS: c180-2.smtp-out.ap-south-1.amazonses.com
Full URL: hxxps://phishmepleaseeehellfire.cf?rid=hs4SqBI
Root Domain: hxxps://phishmepleaseeehellfire.cfIf I were a SOC Analyst, I would have blocked the root domain (this eliminates the possibilities of the same email coming from a subdomain of the same root domain), and the sender's email where this email came from. I would have avoided the IP blocking because the attacker might have spoofed this IP.
Wuahahahahahhahahahahaha!!!
Scenario #2
Okay, scenario two. I am a SOC Analyst at Esmoud Inc. (fake company). Today we received an email from a person called dududu..., lmao. This email appears to come from our Lazy Admin stating something regarding COVID-19 Infected Employees Data (The Subject), along with an attachment named Employees Data.doc,

Alrightty, so let's start analyzing the .eml file. We need to gather artifacts as we did before,
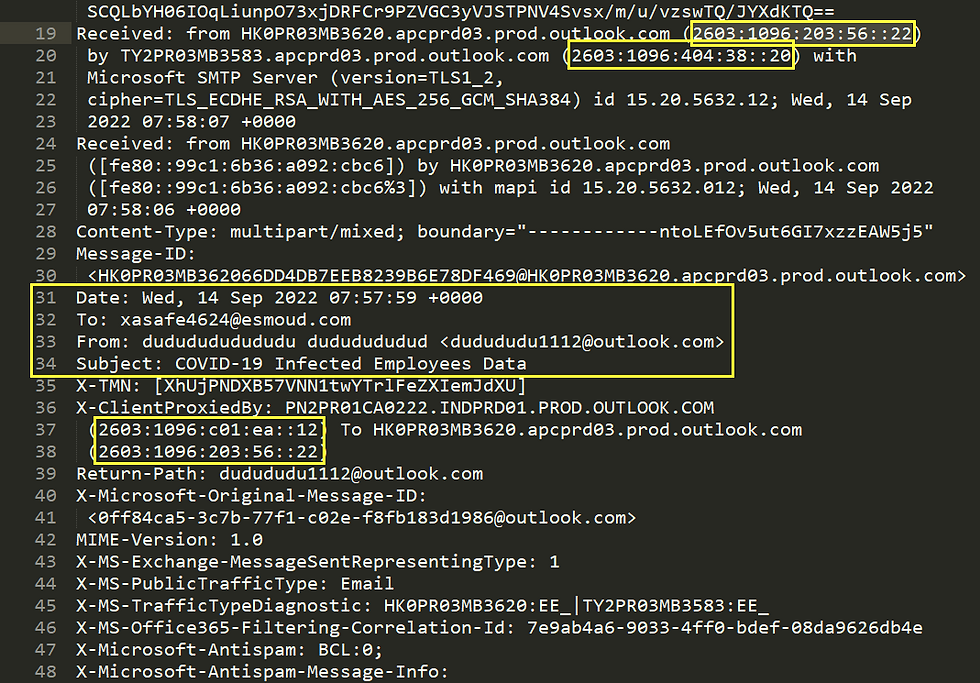
But, in this case, we have IPv6 address here. So searching for it shows us that resolving host is from Microsoft Corporation, meaning it is from Microsoft SMTP Server,

We are done with gathering the IOCs, and all now left is to identify the persona of this doc file. Its content is encoded in Base64,

I have downloaded this .doc file on my Kali VM. Using file command, we can view the properties of this document file. Seems like it is a legit document file which can only be open on Windows OS. If you look at the last line Number of Pages: 1, Number of Words: 7, Number of Characters: 43, it looks very strange because this document should contain the data of the infected employees with full name, but there are only 7 words. Hmmm....(SUSSSSS!!!)
file Employees\ Data.doc
Now, I retrieved the MD5, SHA1, and SHA256 hashes of this file,
md5sum Employees\ Data.doc; sha1sum Employees\ Data.doc; sha256sum Employees\ Data.doc
I pasted one of these hashes on VirusTotal. Out of 62 Anti-Virus, 34 marked it as Trojan, meaning it is highly malicious. With this, we can confidently say that this document should not be open on any Windows Environment. You can see the full report.

The artifacts we collected from this email are present here,
Date & Time: Wed, 14 Sep 2022 07:57:59 +0000
Recipient's Address: xasafe4624@esmoud.com
Sender's Address: dudududu1112@outlook.com
Subject-Line: COVID-19 Infected Employees Data
IP(IPv6) Address: 2603:1096:203:56::22
Reverse DNS: Microsoft SMTP Server
Attachment Name: Employees Data.doc
MD5 - aca8bd3393b416ad8974a4834d548b8e
SHA1 - 7a8570ef93df2c1f5a455e3f4b2c20c370aef3fa
SHA256 - 9370d6612c96826750e8de0f22991b1a3ce55e4c2a7837b5f2992dee516a231cAfter determining that this email is malicious in nature, our work here is not finished. We have to make a request to block the hashes of the attachment on the EDR (Endpoint Detection and Response), blocking the Subject-Line on the Email Gateway, blocking the sender's address on the Email Gateway.
Note: Notice how I have defanged the url by placing X in hxxps. This is done to ensure that url become un-clickable, even if you click on it by-mistake. Always have a habit of defanging malicious URLs. If you want to know what is URL Defanging, I wrote a blog on this.
Make Internet a better place
Since we are talking about how we can analyze phishing emails, we also need to go one step ahead after determining if it is malicious or not, which is to report such malicious link.
Doesn't matter if we are from CyberSecurity, Developing, Finance, etc. We all need to make internet a better, and safer place. Anyone can be phished. Anyone can click on link that might prove to be their nightmare. And to stop all of these, we need to get educated on how to tackle such attacks. It doesn't necessarily means we need to get into CyberSecurity; just foundational training on having a upper hand from these kinds of attacks will make you much from strong.
Below are some links where you can report such malicious link,
With this, we are done with how to analyze phishing emails. Get educated with how to deal with Phishing Attacks. And lastly, please do play your role in making internet a better place for everyone. In the next part, Part 4: we will generate undectectable malicious document for our phishing emails. Peace out.



Comments